Triple Des Encryption Key Generator
The all-in-one ultimate online toolbox that generates all kind of keys! Every coder needs All Keys Generator in its favorites! It is provided for free and only supported by ads and donations. In cryptography, Triple DES (3DES or TDES), officially the Triple Data Encryption Algorithm (TDEA or Triple DEA), is a symmetric-key block cipher, which applies the DES cipher algorithm three times to each data block. The Data Encryption Standard's (DES) 56-bit key is no longer considered adequate in the face of modern cryptanalytic techniques and supercomputing power. Triple DES: DES « Security « Java. Home; Java; 2D Graphics GUI; 3D; Advanced Graphics; Ant; Apache Common; Chart. // Check to see whether there is a provider that can do TripleDES // encryption. If not, explicitly install the SunJCE provider. Throws NoSuchAlgorithmException // Get a key generator for Triple DES (a.k.a DESede). TripleDES Encryption In C#.NET provides high level classes for various encryption algorithms, both symmetric and asymmetric. Data Encryption Standard (DES) is one of the symmetric encryption algorithms that allows both parties, sender and receiver, to use same key to encrypt and decrypt data. The outer two encryption layers can be joined into a single cipher, which we may call DES 2. That is a 64-bit block cipher with a 56-bit key, just like DES. It is approximately twice as expensive to compute. The question then becomes the simple case of applying the meet-in-the-middle attack to double encryption. The inner cipher is DES, the. The all-in-one ultimate online toolbox that generates all kind of keys! Every coder needs All Keys Generator in its favorites! It is provided for free and only supported by ads and donations. Create your hashes online. Calculate a DES hash from your data like passwords or upload a file to create a checksum with the DES encryption algorithm. If you provide an optional salt, you can override the automatic salt generation of the tool.
- Cryptography Tutorial
- Cryptography Useful Resources
- Selected Reading
The Data Encryption Standard (DES) is a symmetric-key block cipher published by the National Institute of Standards and Technology (NIST).
DES is an implementation of a Feistel Cipher. It uses 16 round Feistel structure. The block size is 64-bit. Though, key length is 64-bit, DES has an effective key length of 56 bits, since 8 of the 64 bits of the key are not used by the encryption algorithm (function as check bits only). General Structure of DES is depicted in the following illustration −
Since DES is based on the Feistel Cipher, all that is required to specify DES is −
- Round function
- Key schedule
- Any additional processing − Initial and final permutation
Initial and Final Permutation
The initial and final permutations are straight Permutation boxes (P-boxes) that are inverses of each other. Key generation algorithm in des. They have no cryptography significance in DES. The initial and final permutations are shown as follows −
Round Function
The heart of this cipher is the DES function, f. The DES function applies a 48-bit key to the rightmost 32 bits to produce a 32-bit output.
Expansion Permutation Box − Since right input is 32-bit and round key is a 48-bit, we first need to expand right input to 48 bits. Permutation logic is graphically depicted in the following illustration −
The graphically depicted permutation logic is generally described as table in DES specification illustrated as shown −
XOR (Whitener). − After the expansion permutation, DES does XOR operation on the expanded right section and the round key. The round key is used only in this operation.
Substitution Boxes. − The S-boxes carry out the real mixing (confusion). DES uses 8 S-boxes, each with a 6-bit input and a 4-bit output. Refer the following illustration −
The S-box rule is illustrated below −
There are a total of eight S-box tables. The output of all eight s-boxes is then combined in to 32 bit section.
Straight Permutation − The 32 bit output of S-boxes is then subjected to the straight permutation with rule shown in the following illustration:
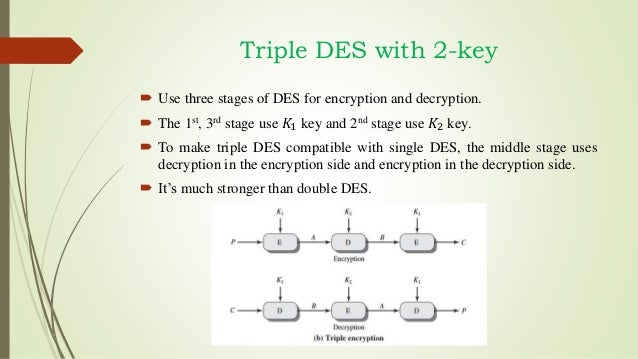
Triple Des Key Generator
Key Generation
The round-key generator creates sixteen 48-bit keys out of a 56-bit cipher key. The process of key generation is depicted in the following illustration −
The logic for Parity drop, shifting, and Compression P-box is given in the DES description.
Des Encryption Tool
DES Analysis
Triple Des Key Length
The DES satisfies both the desired properties of block cipher. These two properties make cipher very strong.
Triple Des Encryption Key Generator Software
Avalanche effect − A small change in plaintext results in the very great change in the ciphertext.
Completeness − Each bit of ciphertext depends on many bits of plaintext. /office-365-home-premium-serial-key-generator.html.
During the last few years, cryptanalysis have found some weaknesses in DES when key selected are weak keys. These keys shall be avoided.
Triple Des Encryption Atm
DES has proved to be a very well designed block cipher. There have been no significant cryptanalytic attacks on DES other than exhaustive key search.