Openssl Generate Public Private Key Pair And Csr
- Openssl Create Private Key
- Openssl Generate Private Key And Csr
- Openssl Generate Public Private Key Pair And Csr Number
- Openssl Generate Public Private Key Pair And Csr 1
- Openssl Generate Public Private Key Pair And Csr Free
- Openssl Create Public Key
Generating a Certificate Signing Request (CSR) using OpenSSL (Apache & mod_ssl, NGINX)
Openssl Create Private Key
A CSR is a file containing your certificate application information, including your Public Key. Generate your CSR and then copy and paste the CSR file into the web form in the enrollment process:
We provides a useful tool to automatically create a public/private key pair on your local machine then use this key pair to generate a CSR and automatically submit it to us over a secure SSL connection to create your certificate for Apache. Or, generate keys and certificate manually. Generate Certificate Signing Request (CSR) for Apache Using OpenSSL. Follow the below instructions to use OpenSSL to create your certificate signing request (CSR) on your Apache server. Step 1: Generating the Private Key. Generate the private key using the below command, provide the passphrase to enhance the security of apache service. Enter CSR and Private Key command. Generate a private key and CSR by running the following command: Here is the plain text version to copy and paste into your terminal: openssl req -new -newkey rsa:2048 -nodes -keyout server.key -out server.csr. Note: Replace “server ” with the domain name you intend to secure. Enter your CSR details. While Encrypting a File with a Password from the Command Line using OpenSSL is very useful in its own right, the real power of the OpenSSL library is its ability to support the use of public key cryptograph for encrypting or validating data in an unattended manner (where the password is not required to encrypt) is done with public keys. While Encrypting a File with a Password from the Command Line using OpenSSL is very useful in its own right, the real power of the OpenSSL library is its ability to support the use of public key cryptograph for encrypting or validating data in an unattended manner (where the password is not required to encrypt) is done with public keys. Generate a Private Key and a CSR. This is the simplest and most common requirement. You first need to generate a public private key pair and also a CSR. The CSR thus generated can be used by Certificate Authority (CA) to produce a SSL certificate. This SSL certificate can then be used to secure the traffic incoming and outgoing from your server.
Generate keys and certificate:
To generate a pair of private key and public Certificate Signing Request (CSR) for a webserver, 'server', use the following command :
This creates a two files. The file myserver.key contains a private key; do not disclose this file to anyone. Carefully protect the private key.
In particular, be sure to backup the private key, as there is no means to recover it should it be lost. The private key is used as input in the command to generate a Certificate Signing Request (CSR).
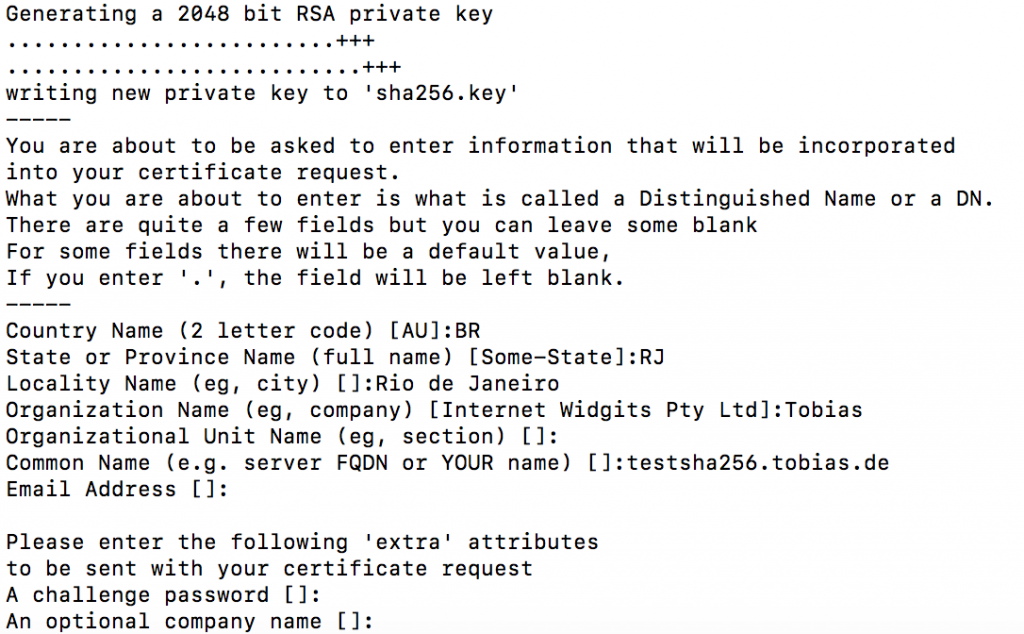
You will now be asked to enter details to be entered into your CSR.
What you are about to enter is what is called a Distinguished Name or a DN.
For some fields there will be a default value, If you enter '.', the field will be left blank.
Please enter the following 'extra' attributes to be sent with your certificate request
Use the name of the web-server as Common Name (CN). If the domain name (Common Name) is mydomain.com append the domain to the hostname (use the fully qualified domain name).
The fields email address, optional company name and challenge password can be left blank for a webserver certificate.
Your CSR will now have been created. Open the server.csr in a text editor and copy and paste the contents into the online enrollment form when requested.
Alternatively one may issue the following command to generate a CSR:
Note: If the '-nodes' is entered the key will not be encrypted with a DES pass phrase.
Related Articles
OpenSSL is a robust, commercial-grade, and full-featured toolkit on the Linux that can be used for a large variety of tasks related to Transport Layer Security (TLS) and Secure Sockets Layer (SSL) protocols. It is also a general purpose cryptography library. It is licensed under an Apache-style license, which basically means that you are free to get and use it for commercial and non-commercial purposes subject to some simple license conditions.
It is already installed out of the box on the most linux distributions or available in the trusted package repositories. OpenSSL has been kind of standard in the open source domain to work with SSL and TLS protocols. If for some reason, it is not already installed, you can install it by using your distribution specific commands.
In this blog post, we’ll learn quick OpenSSL commands that can be used to solve common everyday scenarios. There might be edge scenarios as well, but the intention is not to cover those. So it includes basic scenarios like generating private keys, certificate signing requests, and certificate format conversion. It also assumes that you are already aware of basic concepts of PKI.
About Certificate Signing Requests
Certificate Signing Requests aka CSR are the files which contains basic information about your infrastructure and public key of a key pair. Private key of the key pair is limited to yourself only. It is used by Certificate Authority aka CA to issue certificates. Both of these components are inserted into the certificate when it is signed.
So in order to generate a certificate, one needs atleast two critical pieces: a private-public key pair and a CSR. Whenever you generate a CSR, you will be prompted to provide information regarding the certificate. This information is known as a Distinguised Name (DN). An important field in the DN is the Common Name (CN), which should be the exact Fully Qualified Domain Name (FQDN) of the host that you intend to use the certificate with.
The other items in a DN provide additional information about your business or organization. If you are purchasing an SSL certificate from a certificate authority, it is often required that these additional fields, such as “Organization”, accurately reflect your organization’s details.
Here is an example of what the CSR information prompt will look like:
Country Name (2 letter code) [AU]:IN
State or Province Name (full name) [Some-State]:Maharashtra
Locality Name (eg, city) []:Pune
Organization Name (eg, company) [Internet Widgits Pty Ltd]: My Organization, Inc
Organizational Unit Name (eg, section) []:Digital Marketing
Common Name (e.g. server FQDN or YOUR name) []:mywebsite.com
Email Address []:admins@myorg.com
If you want to non-interactively answer the CSR information prompt, you can do so by adding the -subj option to any OpenSSL commands that request CSR information. Here is an example of the option, using the same information displayed in the code block above:
-subj “/C=IN/ST=Maharashtra/L=Pune/O=My Organization, Inc/CN=phoenix.myorg.com”
It is also possible to skip the interactive prompts when creating a CSR by passing the information via command line or from a file.
Generate CSR
As discussed above, CSRs are needed to request SSL certificates from a certificate authority. Also we need to keep in mind that you may add the CSR information non-interactively with the -subj option, mentioned in the previous section.
Generate a Private Key and a CSR
This is the simplest and most common requirement. You first need to generate a public private key pair and also a CSR. The CSR thus generated can be used by Certificate Authority (CA) to produce a SSL certificate. This SSL certificate can then be used to secure the traffic incoming and outgoing from your server.
Below command creates a 2048-bit private key (mywebsite.key) and a CSR (mywebsite.csr) from scratch:
openssl req
-newkey rsa:2048
-nodes
-keyout mywebsite.key
-out mywebsite.csr
Once above command is input, OpenSSL will prompt few basic questions to fill the Organization specific information. You’ll need to provide the same for it to get completed.
The -newkey rsa:2048 option specifies that the key should be 2048-bit, generated using the RSA algorithm. The -nodes option specifies that the private key should not be encrypted with a pass phrase. The -new option, which is not included here but implied, indicates that a CSR is being generated. If your CA supports SHA-2, add the -sha256 option to sign the CSR with SHA-2.
At end of this command, you’ll have two files created in the current working directory. One of them will have .key extension, which is the private key part of the key pair. Second one will have .csr extension, which is the CSR.
Generate CSR from an existing Private Key
You may already have an existing key pair with you and you would like to use the same for requesting certificate. In this case, you can use below command:
openssl req
-key mywebsite.key
-new
-out mywebsite.csr
Again, once above command is input, OpenSSL will prompt few basic questions to fill the Organization specific information. You’ll need to provide the same for it to get completed.
The -key option specifies an existing private key (mywebsite.key) that will be used to generate a new CSR. The -new option indicates that a CSR is being generated.
Generate CSR from an existing Certificate and Private Key
This method can be used if you want to renew an existing certificate but you or your CA do not have the original CSR for some reason. In fact, most of the Certificate Authority do not store this information. It basically saves you the trouble of re-entering the CSR information, as it extracts that information from the existing certificate. In this case, you can use below command:
openssl x509
-in mywebsite.crt
-signkey mywebsite.key
-x509toreq
-out mywebsite.csr
The -x509toreq option specifies that you are using an X509 certificate to make a CSR.
About Certificates and Self Signed Certificates
To get your certificate signed by 3rd party Certificate Authority, you need to undergo a certain process and pay some money in lieu of their service. If your servers are in the public domain or your service is public facing, then you need to get your certificate signed by well known CAs which are accepted by major browsers and Operating Systems.
Openssl Generate Private Key And Csr
/erlang-crypto-generatekey-rsa.html. It may happen that you do not want to undergo this process for one or the other reasons, then a valid and accepted solution is to sign your own certificates. This is particularly helpful during the development and testing stages of software lifecycle.
When you issue yourself a certificate, it is called as a self-signed certificate. A self-signed certificate is a certificate that is signed with its own private key. Self-signed certificates can be used to encrypt data just as well as CA-signed certificates, but your users will be displayed a warning that says that the certificate is not trusted by their computer or browser.
Therefore, self-signed certificates should only be used if you do not need to prove your service’s identity to its users (e.g. non-production or non-public servers). More often than not, you would be end up using self signed certificates and most probably reading this blog post just for that.
Generate Self-Signed Certificate
Below command can be used to create a 2048-bit private key (mywebsite.key) and a self-signed certificate (mywebsite.crt) in one go:
openssl req
-newkey rsa:2048
-nodes
-keyout mywebsite.key
-x509
-days 365
-out mywebsite.crt
You’ll need to answer the questions prompted to complete the process.
The -x509 option tells req to create a self-signed cerificate. The -days 365 option specifies that the certificate will be valid for 365 days. A temporary CSR is generated to gather information to associate with the certificate.
Generate a Self-Signed Certificate from an existing Private Key
Below command can be used to generate a self signed certificate if you already have a private key:
openssl req
-key mywebsite.key
-new -x509
-days 365
-out mywebsite.crt
You’ll need to answer the questions prompted to complete the process.
The -x509 option tells req to create a self-signed certificate. The -days 365 option specifies that the certificate will be valid for 365 days. The -new option enables the CSR information prompt.
Generate Self-Signed Certificate from an existing Private Key and CSR
Below command can be used to create a self-signed certificate (mywebsite.crt) from an existing private key (mywebsite.key) and (mywebsite.csr):
openssl x509
-signkey mywebsite.key
-in mywebsite.csr
-req
-days 365
-out mywebsite.crt
Since CSR already stands generated, there will be no prompts for asking Organization specific information.
The -days 365 option specifies that the certificate will be valid for 365 days.
View and Verify Certificates, CSR and Keys
Certificate and CSR files are encoded in PEM format, which is not human-readable. Therefore, in order to verify that our CSR/Certificate contains the intended information, openssl provides certain commands.
View CSR Entries
Below command allows you to view and verify the contents of a CSR (mywebsite.csr) in plain text:
openssl req
-text -noout -verify
-in mywebsite.csr
View Certificate Entries
Below command allows you to view the contents of a certificate (mywebsite.crt) in plain text:
openssl x509
-text -noout
-in mywebsite.crt
Verify a Certificate was Signed by a CA
Below command can be used to verify that a certificate (mywebsite.crt) was signed by a specific CA certificate (ca.crt):
openssl verify
-verbose -CAFile ca.crt mywebsite.crt
Verify a Private Key
Below command can be used to check that a private key (mywebsite.key) is a valid key:
openssl rsa
-check
-in mywebsite.key
If your private key is encrypted, you will be prompted for its pass phrase. Upon success, the unencrypted key will be output on the terminal.
On a related note, below command can be used to generate a private key:
openssl genrsa
-des3
-out mywebsite.key 2048
Enter a password when prompted to complete the process. You can also choose to leave it empty.
Verify a Private Key Matches a Certificate and CSR
Below commands can be used to verify if a private key (mywebsite.key) matches a certificate (mywebsite.crt) and CSR (mywebsite.csr):

openssl rsa -noout -modulus -in mywebsite.key openssl md5
openssl x509 -noout -modulus -in mywebsite.crt openssl md5
openssl req -noout -modulus -in mywebsite.csr openssl md5
If the output of each command is identical there is an extremely high probability that the private key, certificate, and CSR are related.
Convert Certificate Formats
Up until now, we have been working with certificates which pertains to X.509 format which encodes information in ASCII format. There are other variety of certificates which are used to encode and decode this information. Some of the applications might require you to provide the certificate in a specific format over others.
Also to be noted that many of these formats can contain multiple items, such as a private key, certificate, and CA certificate, in a single file.
OpenSSL can be used to convert certificates to and from a large variety of these formats.
Convert PEM to DER
Below command can be used to convert a PEM-encoded certificate (mywebsite.crt) to a DER-encoded certificate (mywebsite.der), a binary format:
openssl x509
-in mywebsite.crt
-outform der
-out mywebsite.der
The DER format is typically used with Java.
Openssl Generate Public Private Key Pair And Csr Number
Convert DER to PEM
Below command can be used to convert a DER-encoded certificate (mywebsite.der) to a PEM-encoded certificate (mywebsite.crt):
openssl x509
-inform der
-in mywebsite.der
-out mywebsite.crt
Convert PEM to PKCS7
Below command can be used to add PEM certificates (mywebsite.crt and ca-chain.crt) to a PKCS7 file (mywebsite.p7b):
openssl crl2pkcs7
-nocrl
-certfile mywebsite.crt
-certfile ca-chain.crt
-out mywebsite.p7b
Note that you can use one or more -certfile options to specify which certificates to add to the PKCS7 file.
PKCS7 files, also known as P7B, are typically used in Java Keystores and Microsoft IIS. They are ASCII files which can contain certificates and CA certificates.
Convert PKCS7 to PEM
Below command can be used to convert a PKCS7 file (mywebsite.p7b) to a PEM file:
Openssl Generate Public Private Key Pair And Csr 1
openssl pkcs7
-in mywebsite.p7b
-print_certs
-out mywebsite.crt
Note that if your PKCS7 file has multiple items in it (e.g. a certificate and a CA intermediate certificate), the PEM file that is created will contain all of the items in it.
Openssl Generate Public Private Key Pair And Csr Free
Convert PEM to PKCS12
Below command can be used to take a private key (mywebsite.key) and a certificate (mywebsite.crt), and combine them into a PKCS12 file (mywebsite.pfx):
openssl pkcs12
-inkey mywebsite.key
-in mywebsite.crt
-export -out mywebsite.pfx
You will be prompted for export passwords, which you may leave blank. Note that you may add a chain of certificates to the PKCS12 file by concatenating the certificates together in a single PEM file (mywebsite.crt) in this case.
PKCS12 files, also known as PFX files, are typically used for importing and exporting certificate chains in Micrsoft IIS.
Convert PKCS12 to PEM
Below command can be used to convert a PKCS12 file (mywebsite.pfx) and convert it to PEM format (mywebsite.combined.crt):
openssl pkcs12
-in mywebsite.pfx
-nodes
-out mywebsite.combined.crt
Note that if your PKCS12 file has multiple items in it (e.g. a certificate and private key), the PEM file that is created will contain all of the items in it.
Openssl Create Public Key
Above commands should cover how most people use OpenSSL to deal with SSL certs.