Gpg Generate Public Key From Private
Updated by LinodeWritten by Linode
- Nov 14, 2019 GPG uses public key encryption wherein you create a key pair: one private or secret key you keep to yourself and one public key you share with your correspondents or the world. The important part of this two-key system is that neither key can be calculated by having the other.
- Apr 08, 2005 GNU gpg is encryption and signing tool. Adblock detected 😱 My website is made possible by displaying online advertisements to my visitors. Ads are annoying but they help keep this website running. It is hard to keep the site running and producing new content when so many people block ads. Please consider Continue reading 'Linux create your own GnuPG private and public key'.
- Feb 26, 2018 GPG is the Gnu Privacy Guard and it is an implementation of OpenPGP (Open Pretty Good Privacy). It is an encryption technique that was originally developed for use in.
- Use the gpg -list-secret-keys -keyid-format LONG command to list GPG keys for which you have both a public and private key. A private key is required for signing commits or tags. A private key is required for signing commits or tags.
Jun 30, 2018 A Practical Guide to GPG – Part 1 Generate Your Keypair Check Your GPG Version. First Let’s check out the version of GPG on your system. Create Your Public/Private Key Pair and Revocation Certificate. Export Your Public Key. Others need your public key to send encrypted message to you.
Contribute on GitHubReport an Issue View File Edit File
What is GnuPG?
GNU Privacy Guard (GnuPG), also known as GPG, is a tool for secure communication that was created by Werner Koch as Free Software under the GNU Project. GnuPG follows the OpenPGP protocol, which defines and standardizes all the necessary components involved in sending encrypted messages–signatures, private keys, and public key certificates. This piece of free software is notably used by journalists around the world to ensure that their sensitive email communication is kept secure and private.
GPG uses a combination of symmetric-key cryptography and public-key cryptography. Public key cryptography is likely already familiar to you since it is the recommended way to authenticate when SSHing in to your Linode. Public-key cryptography uses a key-pair system where any single user has a private and public key pair. The public key can be shared with anyone, while the private key should be protected and secret to maintain the integrity of the system.
This asymmetric cryptographic system is ideal for secure communication, because all it requires is that the sender of the message have a copy of the receiver’s public key before encrypting and sending the message. The recipient can then use their private key to decrypt the message. This means anyone can send you a secure message if they have a copy of your public key.
This guide shows how to create your own keypair, distribute the public key to a receiver, and encrypt and decrypt a message on Ubuntu 16.04 and 18.04.
Create GPG Keys
Download and install the most recent version of the GPG command line tools for Ubuntu:
Create a new primary keypair:
Several prompts will appear before the keypair is generated:
- Select
(1) RSA and RSA (default)for the type of key. - Enter
4096for the key size. - Specify the duration the key should be valid in days, weeks, months, or years. For example,
1ywill set an expiration date of one year from the time of keypair creation. - Enter a name, email address, and comment to associate with the key pair. Any one of these three values can be used to identify the keypair for future use. Enter the desired information for each value and confirm when prompted.
- Provide a passphrase. The passphrase is used to unlock the private key, so it is important to ensure the passphrase is strong. Use a mix of alphanumeric characters.
Once you have responded to all prompts, the keypair will be generated. This may take a few minutes to generate depending on the key size that was chosen.
Guitar pro 6 key generator mac. If your system seems to hang at the following message:
The system may require more entropy to generate the keypair, in a new shell session, install the
rng-utilspackage:Check and feed random data from an entropy source (e.g. hardware RNG device) to an entropy sink (e.g. kernel entropy pool) to provide the needed entropy for a secure keypair to be generated:
Check the amount of entropy available on your Linode. The value should be somewhere near 3000 for keypair generation.
- Select
Verify the keys on your public keyring:
The example output contains two public keys:
Each value in the list represents the following information:
- Public key:
pub - Key size and type:
4096R - Short key ID:
A11C0F78 - Creation date:
2018-08-02 - Expiration date:
[expires: 2018-09-01] - User IDs:
exampleName2 (example comment) <[email protected]> - Subkey:
sub
- Public key:
Throughout the remainder of this guide, the first public key will be used to encrypt our message. The output may vary slightly depending on the version of Ubuntu you are using.
Generate a Revocation Certificate
A revocation certificate is useful if you forget your passphrase or if your private key is somehow compromised. It is used to notify others that the public key is no longer valid. Create the revocation certificate immediately after generating your public key.
Generate a revocation certificate. Replace [email protected] with the email address associated with the public key:
- A prompt will ask you to select a reason for the revocation and provide an optional description. The default reason is recommended.
- The revocation certificate will be saved to the current directory as a file named
revoke.asc. Save the certificate to a safe location on a different system so that you can access it in case your key is compromised in the future.
Once you’ve revoked a public key it cannot be used to encrypt future messages to you. It can still be used to verify signatures that you made in the past and to decrypt past messages sent to you.
Exchange Public Keys
You will need to exchange public keys with someone in order to securely communicate with them. If you do not want to make your key available on a key server, you can exchange keys with someone directly by exporting your public key and sending them directly to the recipient.
Export Your Public Key
Export the public key. Replace
public-key.gpgwith a desired name for the file and[email protected]with the email address associated with your key’s user id:The file will save to the current directory.
Send the
public-key.gpgfile to the recipient in an email or copy and paste the contents of thepublic-key.gpgfile.The recipient should import the public key and validate it in order to use it to decrypt a message sent by you.
Import and Validate a Public Key
You can add someone else’s public key to your public keyring by importing it. The user’s public key must first be sent to you, by email or some other format, before you can import it to your public key ring. When the key is imported you should verify the key by checking its fingerprint and then signing it.
Once you’ve received the user’s public key and the
.gpgfile is saved to your Linode, import it to your public key ring. Replacepublic-key.gpgwith the file name of the public key you will import. If your file is saved somewhere other than the current directory, make sure you use the full path to the file:Verify that the public key has been added to your public key ring:
Check the key’s fingerprint:
The output will resemble the following
Ask the owner of the public key to send you their public key’s fingerprint and verify that the fingerprint values match. If they match, you can be confident that the key you have added is a valid copy of the owner’s public key.
When you have verified the public key’s fingerprint, sign the public key with your own key to officially validate it. Replace
[email protected]with the associated email for the key you are validating:Enter your passphrase when prompted.
View the public key’s signatures to verify that your signature has been added:
You can export the signature to the public key and then send the signed copy back to the owner of the public key to boost the key’s level of confidence for future users:
Send the signed key to the public key owner via email so they can import the signature to their GPG database.
Submit Your Public Key to a Key Server
You can submit your public key to a GPG server to make it available to the general public. The GnuPG configuration file ~/.gnupg/gpg.conf by default sets the key server as hkp://keys.gnupg.net and provides examples of other key servers that can be used in the file’s comments. Since key servers around the globe synchronize their keys to each other it should not be necessary to change the default value set in the configuration file.
Find the long key ID for the public key you would like to send to the key server:
You will see an output similar to the example. The long key ID is the value after the key size
4096Rin thepubrow. In the example the long key ID isC7277DE1A11C0F78:To send your public key to the default key server use the following command and replace
keyidwith your public key’s long key ID:Anyone can request your public key from the key server with the following command:
The public key will be added to the user’s trust database using the
trustdb.gpgfile.
Encrypt a Message
After you have obtained someone’s public keys, you can send them encrypted messages. When you are encrypting a message to send to someone, you are using their public key to encrypt the message. Only the holder of the corresponding private key will be able to decrypt the message.
To encrypt a message:
Replace encrypted-doc.gpg with a name for the encrypted version of your document, [email protected] with the email associated with the public key of the encrypted message’s recipient, [email protected] with your own public key’s associated email and doc-to-encrypt.txt with the name of the document you will encrypt. If the document is not in the current directory, include the full path to the document.
The extension .gpg is used for encrypted/binary data and .asc or .sig is used for detached or clearsign signatures. Including the --armor flag will encrypt the message in plain text.
Decrypt a Message
A message will need to have been encrypted with your public key for you to able to decrypt it with your private key. Ensure that anyone that will be sending you an encrypted message has a copy of your public key.
To decrypt a message:
Replace decrypted-doc with the name you want to assign to the decrypted message and doc-to-decrypt.gpg with the name of the encrypted document. If the document is not in the current directory, include the full path to the document.
More Information
You may wish to consult the following resources for additional information on this topic. While these are provided in the hope that they will be useful, please note that we cannot vouch for the accuracy or timeliness of externally hosted materials.
Join our Community
This guide is published under a CC BY-ND 4.0 license.
Updated by Alex FornutoContributed byHuw Evans
Report an Issue View File Edit File
You may be familiar with public key authentication for Secure Shell (SSH) on your Linode. But you may not have known that you can also use a GNU Privacy Guard (GPG) keypair to authenticate with SSH.
The chief benefit of this method is that instead of having separate keys for GPG messaging and SSH authentication, they can both belong to the same GPG keyring. This configuration really shines, however, when used with a GPG smartcard or YubiKey, because the card/dongle can store the underlying private key and only authenticate SSH sessions when it’s plugged in. WIRED reported that engineers at Facebook use this method for authenticating with local servers, so why shouldn’t you?
This guide will show you how to generate a GPG key, set up your computer to serve it in place of an SSH key, and put the new public key onto your server for authentication. It will also detail how to optionally move your GPG private key onto a smartcard or YubiKey to prevent authentication when the device isn’t plugged into your computer.
Before You Begin
NoteThis guide assumes:
- You have a fully functional Linode
- You have followed the Getting Started and Securing Your Server guides, and updated your Linode with
sudo apt-get update && sudo apt-get upgrade) - You are familiar with the command line
You don’t necessarily need to be familiar with SSH public key authentication or GPG encryption, but an understanding of their operation will help you out if you run into problems.
Generate a GPG Keypair
This section explains how to generate a new GPG keypair. If you already have one, you may skip these steps, as the next section will include instructions for how to create a subkey to use specifically for authentication. You will just need the 8-digit ID for your existing key to do so.
CautionAll of these steps should be performed on a local machine, not your Linode.
Install GPG:
On Debian and its derivatives:
On OS X:
GPGTools provides the simplest implementation of GPG for OS X. Otherwise, you could run
brew install gnupg2if you have Homebrew.On other operating systems, this process should be fairly clear. GPG is likely already installed, but if it isn’t, a quick internet search should give you the instructions you need.
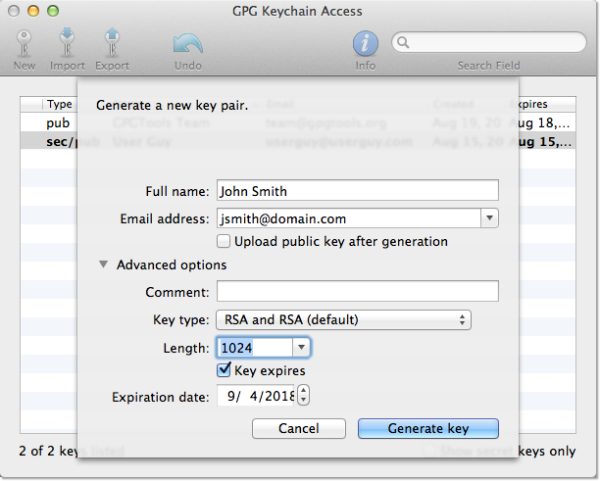
Open a command prompt and execute:
When prompted to select the kind of key you want, select
(1) RSA and RSA.When asked for a keysize, type
4096. If you want to store your key on a YubiKey Neo or certain smartcards, you may be restricted to a 2048-bit key size, so ensure that you aware of limitations for your device, if applicable.Choose an expiration period that you think will be suitable for this key. After that date, the key will no longer work, so choose carefully.
Enter your full name, email address, and a comment (if you want). Select
Ofor ‘Okay’.After looking over your shoulders for secret agents, enter a long and secure passphrase that will be used to encrypt your key in local storage. Write this down somewhere you know to be physically secure while your computer generates the keypair.
Once this is done, your output should resemble the following:
Gpg Export Public Key From Private Key
This process has created a master GPG key and a subkey for encrypting messages and files. To authenticate with SSH, we need to generate a second subkey for authentication.
Generating the Authentication Subkey
In a command prompt or terminal, type:
Replace
key-idwith the eight-character string output from the key generation process. This will be found in the line beginning withpub. In the example above, the ID is71735D23.At the new
gpg>prompt, enter:When prompted, enter your passphrase.
When asked for the type of key you want, select:
(8) RSA (set your own capabilities).Enter
Sto toggle the ‘Sign’ action off.Enter
Eto toggle the ‘Encrypt’ action off.Enter
Ato toggle the ‘Authenticate’ action on. The output should now includeCurrent allowed actions: Authenticate, with nothing else on that line.Enter
Qto continue.When asked for a keysize, choose
4096. The same limitation from Step 4 in the first section applies, so ensure your card/YubiKey can support this key size.Enter an expiration date, just as before. You should probably keep this the same as the first one. If you choose a lower expiration date, your main private key will continue to function but your SSH authentication will break on this date.
When you’re sure all of the information entered is correct, enter
yat theReally create? (y/N)prompt to complete the process.Once the key is created, enter
quitto leave the gpg prompt, andyat the prompt to save changes.
Your terminal should now look like this:
Secure Your GPG Key
CautionYou should always have a backup of your private key in case something goes wrong and you end up locked out of everything that requires it. This private key, along with the instructions in this guide, will be enough to get your setup working again if you need to start afresh on a new computer.
Back up your
~/.gnupgfolder with the following command, replacingUSB_DEVICEwith the name of your device:This assumes you have a storage device mounted at
/Volumes/USB_DEVICE/. Different operating systems may use different naming conventions for this path. You can safely ignore anyOperation not supported on socketwarnings that appear when you enter this command.Back up your private key, replacing
key-idwith the eight-character key ID for your private key:Back up your subkeys, replacing
key-idwith the eight-character key ID for each subkey:
If something bad happens and you lose your keys, you can re-import them by overwriting the ~/.gnupg directory with your copy, and using:
Be sure to replace key-file with the location of each of your files.
Export Your Public Key
If you’re working on a VM or offline machine, you’ll also need to export your public key to be reimported later:
Be sure to replace key-id with your own key ID.
You can reimport it with the ever-handy gpg2 --import key-file command.
Move Your Key to a Smartcard or YubiKey (Optional)
Noteykpersonalise -m82. ykpersonalise can be installed through your package manager.Secure Your Card
It is assumed that you have already configured your card/YubiKey’s (herein referred to as ‘GPG device’) owner information. It is highly recommended that you secure your card before you start this section.
Note123456, and the default Admin PIN is usually 12345678. If these don’t work, contact the manufacturer or review online documentation.Gpg Generate Public Key From Private Schools
Plug in the device and execute:
Enable admin commands:
Enter the password change menu:
Change the password to your device by selecting
2 - unblock PIN. This will unblock your PIN, and prompt you to change it. This PIN will be required every time you want to access your GPG key (e.g. every time you authenticate with SSH), and has a limit of eight characters.Change the admin PIN by selecting
3 - change Admin PIN. This PIN is required to make administrative changes, like in step 2, and has a limit of 6 characters. For optimum security, never store this PIN in a digital location, since it will be unnecessary for daily use of the YubiKey.Exit these menus by selecting
Qand then typingquit.
For reference, your window should resemble the following. This example is abbreviated:
Transfer Your Subkey
Gpg Generate Key Pair
Enter the key edit menu from a normal command prompt, replacing
key-idwith your own key ID:Switch to the private key editor:
Select only the authentication subkey:
Remember, if you have more subkeys this command should be changed as appropriate.
Transfer the key:
Select
(3) Authentication keyto store your key on the third slot of the device. If this is not an option, ensure that you’ve selected the appropriate subkey.Enter your passphrase.
Type
saveto exit this menu.If you’re working on a VM or offline machine, export the subkey stubs (pointers so GPG knows your subkeys are on the device):
Be sure to substitute your own key ID for
key-id. You can reimport these with an ordinarygpg2 --import <stub file>on your private machine.
After all this, your output should resemble the following:
Congratulations! You’ve successfully transferred your authentication subkey to your device.
CautionServe Your GPG key Instead of an SSH key
In this section, we’ll configure your local machine so the connection between GPG and SSH works properly.
Return to your local machine, import all of the appropriate GPG keys and insert the appropriate GPG device. Install GPG if you don’t already have it on your local computer (e.g. if you performed all the above steps on a VM).
Edit the
~/.bash_profilefile (or similar shell startup file) to include:Linux:
- ~/.bash_profile
OS X
- ~/.bash_profile
This ensures that SSH can ‘see’ your GPG keys and automatically starts
gpg-agentas needed.Edit or create
~/.gnupg/gpg-agent.conf:- ~/.gnupg/gpg-agent.conf
If you’re on OS X and previously installed GPGTools, you can also add the line:
This allows you to use the PIN entry program provided by GPGTools.
Restart the GPG agent:
Add the New Key to Your Linode
The steps from the previous sections will take your GPG keys and pipe them through SSH so they can be used for authentication. The result of this process is that you’ve created a new RSA public key for use with SSH authentication.
Private Key
On your local machine, extract the public key:
You should see a long output of alphanumeric characters. If you see
The agent has no identities, try the steps to restart the GPG agent from above.Copy the whole string of output, including
ssh-rsa. If you see multiple strings beginning withssh-rsa, copy the one that ends withcardno:. It might look like this:Paste this into a new file (for example,
~/gpg-key.pub) and save it.Copy the file to your Linode:
Log into your Linode and append the key to the
authorized_hostsfile:
You’re done! Disconnect, and all new logins should now use your GPG key instead of a passphrase. This SSH key can also be used with GitHub, Bitbucket, other SSH-based Version Control Systems, or anywhere else that accepts SSH keys.
More Information
You may wish to consult the following resources for additional information on this topic. While these are provided in the hope that they will be useful, please note that we cannot vouch for the accuracy or timeliness of externally hosted materials.
Join our Community
This guide is published under a CC BY-ND 4.0 license.