Generate Server Admin Privilege Key
This article shows you how to create a new Azure Active Directory (Azure AD) application and service principal that can be used with the role-based access control. When you have code that needs to access or modify resources, you can create an identity for the app. This identity is known as a service principal. You can then assign the required permissions to the service principal. This article shows you how to use the portal to create the service principal. It focuses on a single-tenant application where the application is intended to run within only one organization. You typically use single-tenant applications for line-of-business applications that run within your organization.
Important
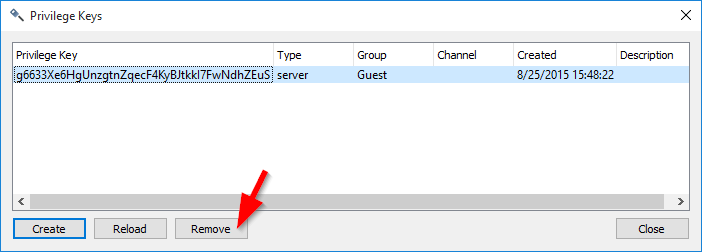
How do I become an administrator or get a server admin privilege key on my server? In order to become a server administrator on your server you will need to generate a 'Server Admin' privilege key/token. Top 4 Download periodically updates software information of administrator privileges full versions from the publishers, but some information may be slightly out-of-date. Using warez version, crack, warez passwords, patches, serial numbers, registration codes, key generator, pirate key, keymaker or keygen for administrator privileges license key is illegal. At the top of TeamSpeak click the 'Permissions' menu then click the 'Privilege Keys' option. Create New Privilege Key Click the 'Create' button to bring up the window that will generate the key. One with the type of Privilege Key it will be and then the group it will belong to. Below that is a white space this is where the Privilege Key will show up once you generate it. Now what you will want to do is press the 'Create' button. This will generate the Privilege Key.
Instead of creating a service principal, consider using managed identities for Azure resources for your application identity. If your code runs on a service that supports managed identities and accesses resources that support Azure AD authentication, managed identities are a better option for you. To learn more about managed identities for Azure resources, including which services currently support it, see What is managed identities for Azure resources?.
Create an Azure Active Directory application
Let's jump straight into creating the identity. If you run into a problem, check the required permissions to make sure your account can create the identity.
Sign in to your Azure Account through the Azure portal.
Select Azure Active Directory.
Select App registrations.
Select New registration.
Name the application. Select a supported account type, which determines who can use the application. Under Redirect URI, select Web for the type of application you want to create. Enter the URI where the access token is sent to. You can't create credentials for a Native application. You can't use that type for an automated application. After setting the values, select Register.
You've created your Azure AD application and service principal.
Assign a role to the application
To access resources in your subscription, you must assign a role to the application. Decide which role offers the right permissions for the application. To learn about the available roles, see RBAC: Built in Roles.
You can set the scope at the level of the subscription, resource group, or resource. Permissions are inherited to lower levels of scope. For example, adding an application to the Reader role for a resource group means it can read the resource group and any resources it contains.
In the Azure portal, select the level of scope you wish to assign the application to. For example, to assign a role at the subscription scope, search for and select Subscriptions, or select Subscriptions on the Home page.
Select the particular subscription to assign the application to.
If you don't see the subscription you're looking for, select global subscriptions filter. Make sure the subscription you want is selected for the portal.
Select Access control (IAM).
Select Add role assignment.
Select the role you wish to assign to the application. For example, to allow the application to execute actions like reboot, start and stop instances, select the Contributor role. Read more about the available roles By default, Azure AD applications aren't displayed in the available options. To find your application, search for the name and select it.
Select Save to finish assigning the role. You see your application in the list of users with a role for that scope.
Your service principal is set up. You can start using it to run your scripts or apps. The next section shows how to get values that are needed when signing in programmatically.
Get values for signing in
When programmatically signing in, you need to pass the tenant ID with your authentication request. You also need the ID for your application and an authentication key. To get those values, use the following steps:
Select Azure Active Directory. Windows xp professional sp2 key generator.
From App registrations in Azure AD, select your application.
Copy the Directory (tenant) ID and store it in your application code.
Copy the Application ID and store it in your application code.
Certificates and secrets
Daemon applications can use two forms of credentials to authenticate with Azure AD: certificates and application secrets. We recommend using a certificate, but you can also create a new application secret.
Upload a certificate
You can use an existing certificate if you have one. Optionally, you can create a self-signed certificate for testing purposes only. Open PowerShell and run New-SelfSignedCertificate with the following parameters to create a self-signed certificate in the user certificate store on your computer:
Export this certificate to a file using the Manage User Certificate MMC snap-in accessible from the Windows Control Panel.
Select Run from the Start menu, and then enter certmgr.msc.
The Certificate Manager tool for the current user appears.
To view your certificates, under Certificates - Current User in the left pane, expand the Personal directory.
Right-click on the cert you created, select All tasks->Export.
Follow the Certificate Export wizard. Do not export the private key, and export to a .CER file.
To upload the certificate:
Select Azure Active Directory.
From App registrations in Azure AD, select your application.
Select Certificates & secrets.
Select Upload certificate and select the certificate (an existing certificate or the self-signed certificate you exported).
Mathematica 11 activation key generator online. Select Add.
After registering the certificate with your application in the application registration portal, you need to enable the client application code to use the certificate.
Create a new application secret
If you choose not to use a certificate, you can create a new application secret.
Select Certificates & secrets.
Select Client secrets -> New client secret.
Provide a description of the secret, and a duration. When done, select Add.
After saving the client secret, the value of the client secret is displayed. Copy this value because you won't be able to retrieve the key later. You will provide the key value with the application ID to sign in as the application. Store the key value where your application can retrieve it.
Configure access policies on resources
Keep in mind, you might need to configure addition permissions on resources that your application needs to access. For example, you must also update a key vault's access policies to give your application access to keys, secrets, or certificates.
- In the Azure portal, navigate to your key vault and select Access policies.
- Select Add access policy, then select the key, secret, and certificate permissions you want to grant your application. Select the service principal you created previously.
- Select Add to add the access policy, then Save to commit your changes.
Required permissions

You must have sufficient permissions to register an application with your Azure AD tenant, and assign to the application a role in your Azure subscription.
Check Azure AD permissions
Select Azure Active Directory.
Note your role. If you have the User role, you must make sure that non-administrators can register applications.
In the left pane, select User settings.
Check the App registrations setting. This value can only be set by an administrator. If set to Yes, any user in the Azure AD tenant can register an app.
If the app registrations setting is set to No, only users with an administrator role may register these types of applications. See available roles and role permissions to learn about available administrator roles and the specific permissions in Azure AD that are given to each role. If your account is assigned the User role, but the app registration setting is limited to admin users, ask your administrator to either assign you one of the administrator roles that can create and manage all aspects of app registrations, or to enable users to register apps.
Check Azure subscription permissions
In your Azure subscription, your account must have Microsoft.Authorization/*/Write access to assign a role to an AD app. This action is granted through the Owner role or User Access Administrator role. If your account is assigned the Contributor role, you don't have adequate permission. You will receive an error when attempting to assign the service principal a role.
Generate Server Admin Privilege Key For Windows 7
To check your subscription permissions:
Search for and select Subscriptions, or select Subscriptions on the Home page.
Select the subscription you want to create the service principal in.
If you don't see the subscription you're looking for, select global subscriptions filter. Make sure the subscription you want is selected for the portal.
Select My permissions. Then, select Click here to view complete access details for this subscription.
Select View in Role assignments to view your assigned roles, and determine if you have adequate permissions to assign a role to an AD app. If not, ask your subscription administrator to add you to User Access Administrator role. In the following image, the user is assigned the Owner role, which means that user has adequate permissions.
Next steps
- To learn about specifying security policies, see Azure Role-based Access Control.
- For a list of available actions that can be granted or denied to users, see Azure Resource Manager Resource Provider operations.
After creating server user account in Windows server 2012 (R2), how to add the user to local administrator group to grant it administrator privileges? This passage will tell you two easy ways to achieve this goal.
The following ways are introduced using server 2012 (R2) computer, and also apply to Windows 7 and Windows server 2008 (R2).
1. Add user to local administrator group via computer management
Step 1: Press Win +X to open Computer Management
Step 2: In the console tree, click Groups.
Computer ManagementSystem ToolsLocal Users and GroupsGroups
Step 3: Right-click the group to which you want to add a member, click Add to Group, and then click Add.
Step 4: In the Select Users (Computers, or Groups) dialog box, do the following:
Server Admin Tools
- To add a user account or group account to this group, under Enter the object names to select , type the name of the user account or group account that you want to add to the group, and then click OK .
- To add a computer account to this group, click Object Types, select the Computers check box, and then click OK. Under Enter the object names to select, type the name of the computer account that you want to add to the group, and then click OK.
2. Add user to local administrator group via net user command
Login into Windows server 2012 (r2) with administrator, and then do as following:
Generate Server Admin Privilege Key Generator
Step 1: Press Win + X to run Command Prompt (Admin).
In other Windows operational systems, you may have to click 'Start', type 'cmd' and press Enter to run command prompt.
Step 2: Type 'net user' command to see what the user accounts are on Windows server 2012 (R2).
Step 3: Type the following command to add user account 'genius' to local administrators group. And press Enter to complete this command.
net localgroup administrators genius /add
Related articles: